Hackers Flood NameCheap Users with Metamask Phishing Attempts
Domain registrar Namecheap experienced a security breach on Sunday night, leading to the sending of phishing emails to their clients. The phishing emails appeared to come from either MetaMask or DHL and attempted to steal recipients’ personal information and cryptocurrency wallets. The phishing campaigns originated from SendGrid, an email platform used by Namecheap, and started around 4:30 PM ET.
⚠️MetaMask does not collect KYC info and will never email you about your account!
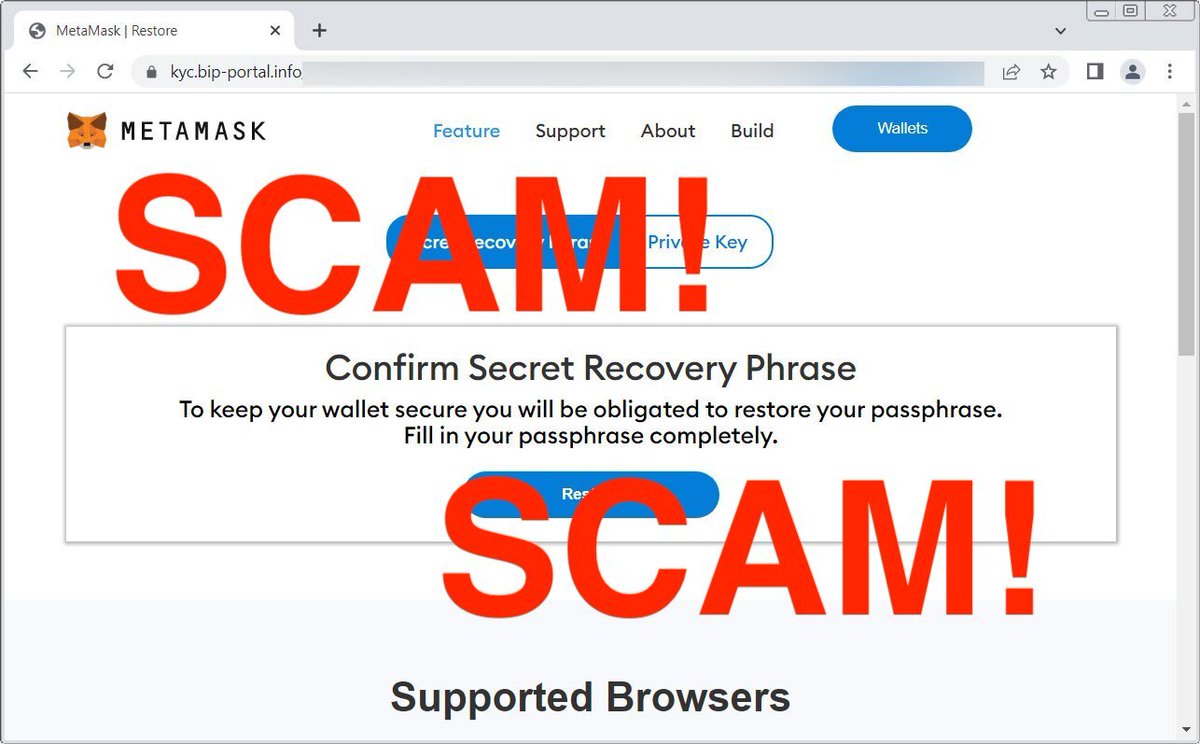
Do not enter your Secret Recovery Phrase on a website EVER.
If you got an email today from MetaMask or Namecheap or anyone else like this, ignore it & do not click its links!https://t.co/EP0HGZFOfo pic.twitter.com/4CDtne24OK— MetaMask 🦊💙 (@MetaMask) February 13, 2023
NameCheap Confirms Email Breach
Recipients of the phishing emails quickly began complaining on social media, leading to a response from Namecheap CEO Richard Kirkendall. Kirkendall confirmed the breach and stated that the company had disabled their email through SendGrid while they investigated the issue. He also suggested that the breach may have been related to a December CloudSek report about exposed API keys in Mailgun, MailChimp, and SendGrid.
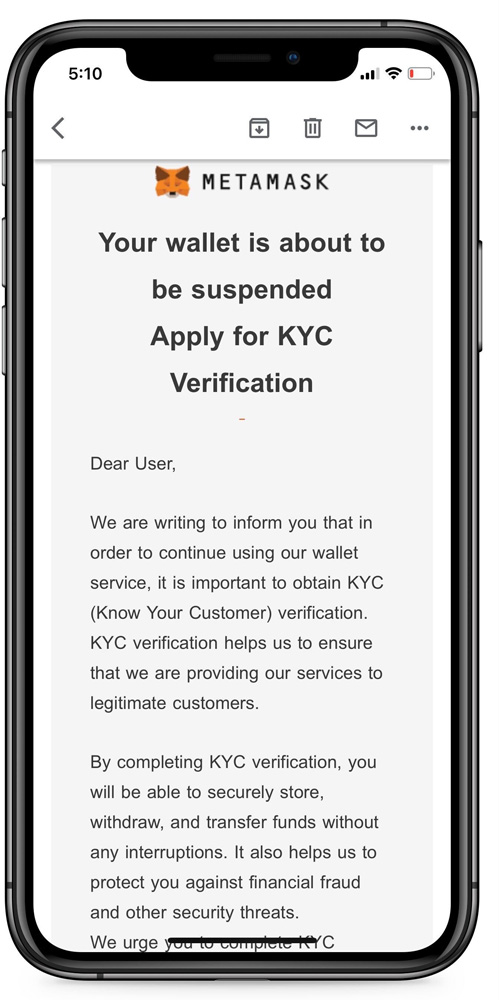
The phishing emails were impersonating either DHL or MetaMask. The DHL phishing email claimed to be a bill for a delivery fee, with links that led to a phishing page trying to steal the recipient’s information. The MetaMask phishing email pretended to be a required KYC verification to avoid suspension of the wallet. The email contained a marketing link from Namecheap that redirected users to a phishing page pretending to be MetaMask. If a user provided either their recovery phrase or private key, the threat actors could use this information to steal all their funds and assets.
Systems Not Breached, Upstream Provider Blamed
Namecheap published a statement claiming that their systems were not breached, but rather the issue was with an upstream system they use for email. They assured clients that their products, accounts, and personal information remained secure. However, Namecheap did not name the upstream system. The CEO of Namecheap had previously tweeted that they were using SendGrid, which was confirmed in the phishing emails’ mail headers. Twilio SendGrid, the provider of the email service, denied any involvement in the breach and stated that it was not the result of a hack or compromise of their systems.
As a result of the phishing incident, Namecheap stopped all emails, including two-factor authentication, trusted device verification, and password reset emails. Services were however restored later at about 7:08 PM EST.



